
The US Treasury Department has sanctioned two individuals affiliated with the Russian ransomware group that stole $9 billion in assets from a US broker-dealer. The software, created by Russia’s LockBit group, likely contributed to the rise in ransomware attacks in 2023.
The US added Russian nationals Artur Sungatov and Ivan Kondratiev to the Office of Foreign Assets Control’s (OFAC) registry of specially designated individuals.
US Treasury Increases Crypto Sanctions
In addition to adding their names to the list, the Treasury Department has also blacklisted ten crypto addresses belonging to the individuals. The sanctions mean US companies and citizens may not transact with the individuals.
All properties belonging to the Russians must also be reported to the US Treasury Department. The latest sanctions are part of the US Treasury’s ongoing effort to crack down on terrorist financing.
It previously blacklisted crypto wallet addresses belonging to the North Korean group Lazarus. The regulator later proposed that altcoin and bitcoin mixers follow the same record-keeping and reporting rules imposed on foreign banks.
Read more: Crypto vs. Banking: Which Is a Smarter Choice?
The US government has warned Russia to take more concrete steps to prevent the operations of terrorist financing from taking place in the country. LockBit, the subject of a seizure by US Attorney General Merrick B. Garland, was a Russian darknet.
How Ransomware Strains Are Evolving
On-chain analysis firm Chainalysis argued that ransomware attacks increased in 2023 to over $1 billion after a dip in 2022. Cybersecurity firm Recorded Future confirmed around 583 new ransomware variants. These variants can threaten cyber and cryptocurrency security.
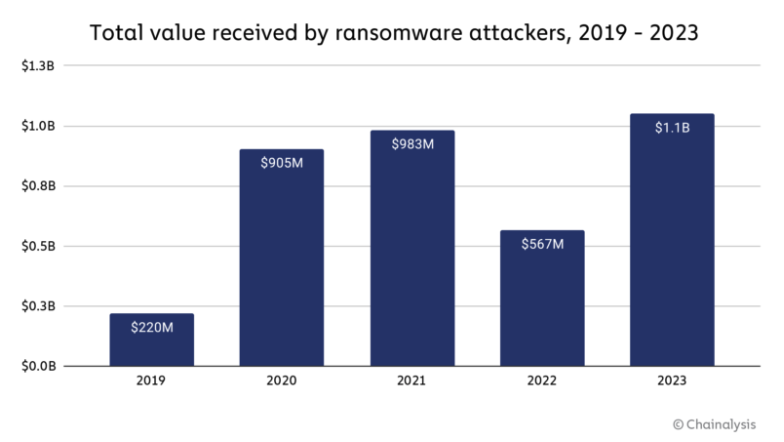
LockBit and Phobos are ransomware strains whose Ransomware-as-a-Service (RaaS) allowed affiliates like Sungatov and Kondratiev to carry out the attacks. Some new entrants copied code from existing strains to reap high profits with minimal investments, while others adopted rebrands to distance themselves from sanctioned entities.
The growth of initial access brokers (IABs) has made it easier for bad actors to conduct ransomware attacks. These entities sell penetrated networks to ransomware attackers for less than $1000.
Read more: 15 Most Common Crypto Scams To Look Out For
The combination of IABs and RaaS creates a ‘disturbingly effective’ business model for criminals, says Andrew Davis of cybersecurity incident response consulting firm Kivu Consulting.
“The increase in attack volume can be attributed to the affiliate model’s ease of access and the adoption of ransomware-as-a-service, a disturbingly effective business model for cybercriminals,” Davis said.
BeInCrypto reached out to the US Treasury Department but had yet to hear back at press time
Disclaimer
In adherence to the Trust Project guidelines, BeInCrypto is committed to unbiased, transparent reporting. This news article aims to provide accurate, timely information. However, readers are advised to verify facts independently and consult with a professional before making any decisions based on this content. Please note that our Terms and Conditions, Privacy Policy, and Disclaimers have been updated.



Be the first to comment